
WEBVIEW跨源攻击分析
漏洞聚焦:CPP和Parity Ethereum客户端中的多个漏洞
http://blog.talosintelligence.com/2018/01/vulnerability-spotlight-multiple.html
[dos] Microsoft Windows – ‘nt!NtQueryInformationProcess (information class 76, QueryProcessEnergyValues)’ 内核栈内存泄露
https://www.exploit-db.com/exploits/43470/
一个生成带有subdoc payload文档的工具
https://github.com/RhinoSecurityLabs/Security-Research/blob/master/tools/ms-office/subdoc-injector/subdoc_injector.py
https://rhinosecuritylabs.com/research/abusing-microsoft-word-features-phishing-subdoc/
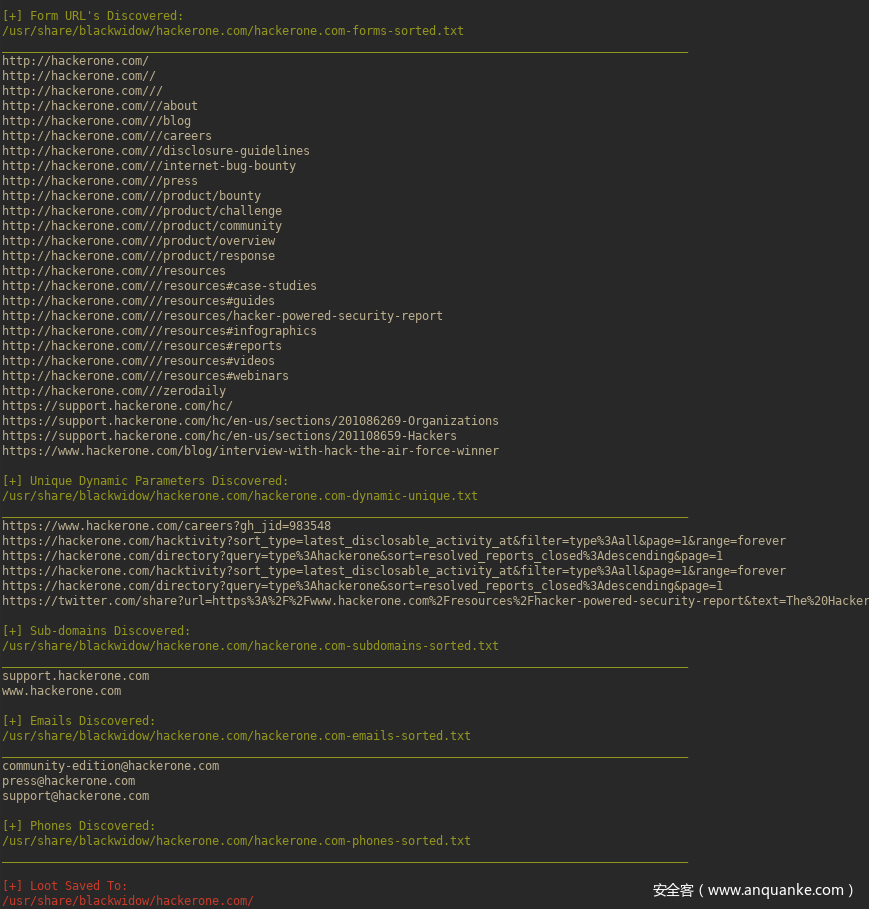
BlackWidow : 一个基于python的web爬虫,用于从目标网站收集子域名,URL,动态参数,电子邮件地址和电话号码
https://github.com/1N3/BlackWidow
https://www.youtube.com/watch?v=mch8ht47taY
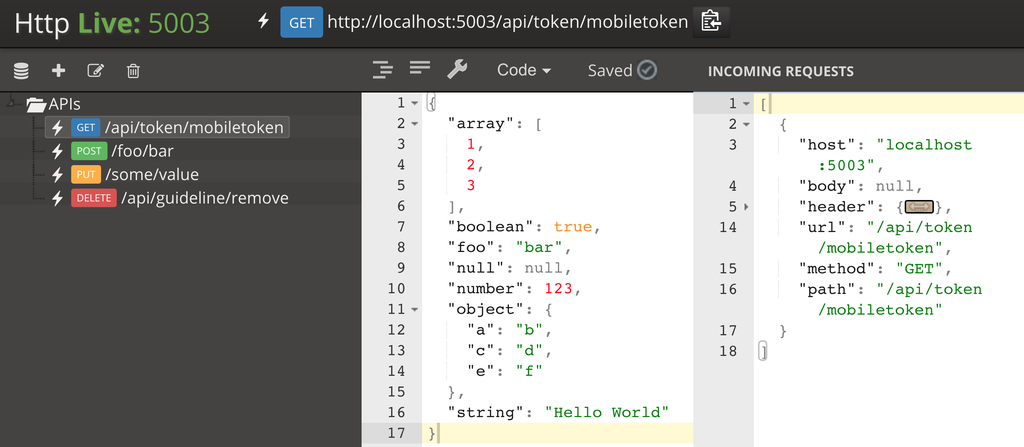
HttpLive:不依赖后端程序的HTTP请求/响应的开发测试工具
https://github.com/gencebay/httplive
[local] Microsoft Windows – Local XPS Print Spooler Sandbox Escape
https://www.exploit-db.com/exploits/43465/
“Web Application Firewall (#WAF) Evasion Techniques”:
https://medium.com/secjuice/waf-evasion-techniques-718026d693d8
https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0
逆向与汇编入门教程
http://kakaroto.homelinux.net/2017/11/introduction-to-reverse-engineering-and-assembly/
The Intel 80×86 Processor Architecture : Pitfalls for Secure Systems :
https://pdfs.semanticscholar.org/2209/42809262c17b6631c0f6536c91aaf7756857.pdf
[dos] Android – Inter-Process munmap due to Race Condition in ashmem
https://www.exploit-db.com/exploits/43464/
https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/43464.zip
Intel Smart Cache Technology Animation
https://www.youtube.com/watch?v=bE9EbQOeb_U
AWS-Scanner:Scans a list of websites for Cloudfront or S3 Buckets
https://github.com/random-robbie/AWS-Scanner/
作者:安全客小编2
如若转载,请注明出处: https://www.anquanke.com/post/id/94240